From online shopping to healthcare to banking and just about everywhere else, APIs are transforming our lives. APIs increase productivity, eliminate manual efforts, streamline business processes and improve customer experiences. They are fundamentally changing the worldwide economy. Yet, with all of that promise comes potential risks. By providing access, APIs open up tempting new security vulnerabilities. According to Gartner, by 2022 APIs will become the leading target of attacks by hackers. Since the IBM i typically runs the core applications of the business, this problem is especially acute for our community.
So how do we take advantage of all the opportunities APIs offer while protecting our systems from attack? There are several areas where you should take action to safeguard your systems.
1. Authentication
As should be obvious, it is critically important to know who is accessing your APIs and to ensure they are an authorized user. Unfortunately, this is not as simple as just asking for a user ID and password. How do you ensure that the user ID and password have not been compromised? I have seen too many IBM i shops that continue to rely on Basic Authentication and use actual IBM i credentials for authentication. Compounding the problem, some shops use 64-bit encoding instead of encryption when attempting to protect those user IDs and passwords.
IBM i users should move away from Basic Authentication and start using JSON Web Token (JWT) based authentication. JWTs use a trusted third party to generate a secure, encrypted token that can only be accessed by the authorized user. Even if a bad actor were to intercept the transmission, all they would get would be an unreadable encrypted string – there are no embedded credentials. It also allows you to use a separate set of credentials that provide no native access to your IBM i.
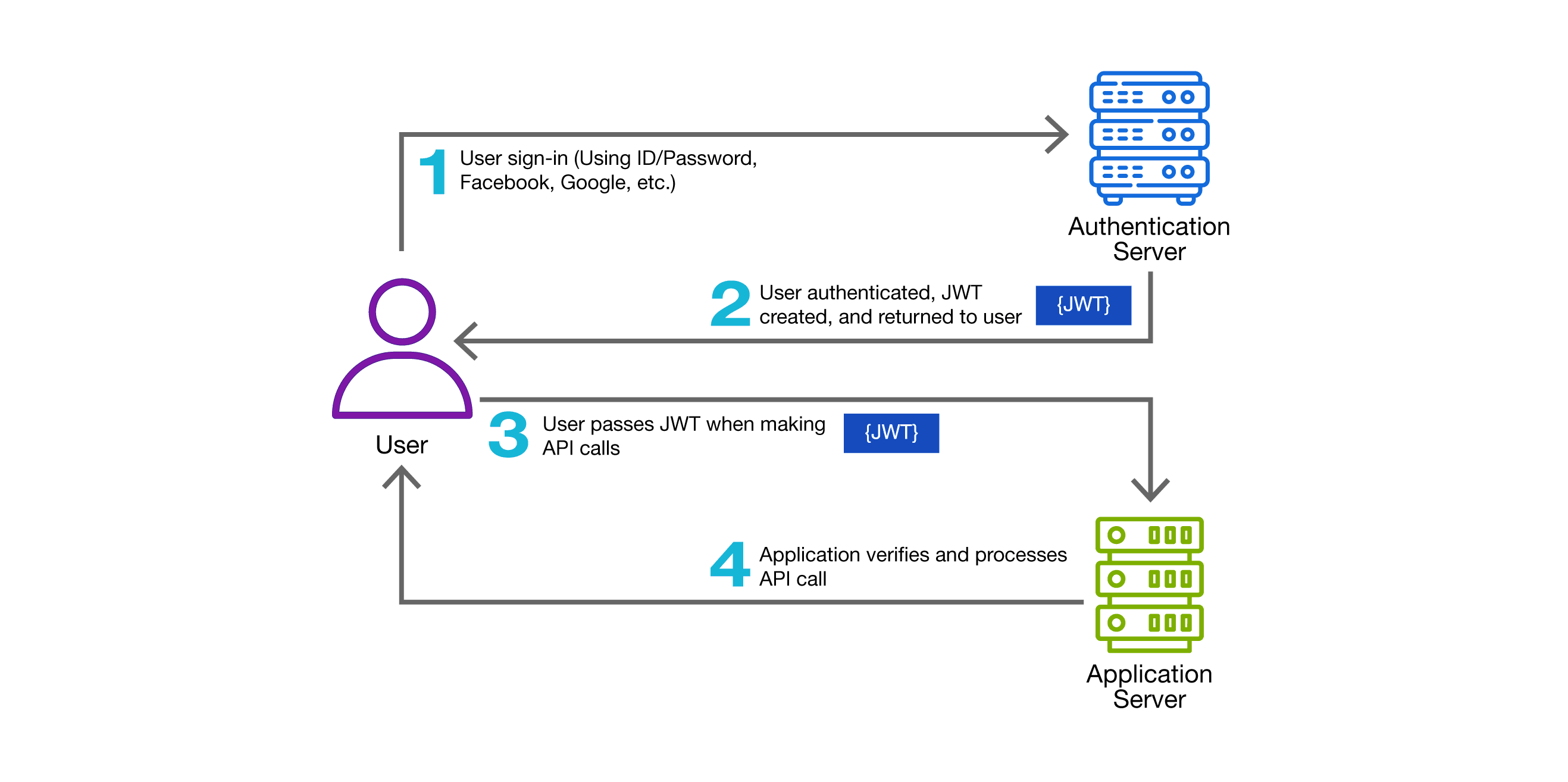
Fortunately, there are readily available, trusted open source modules you can use to implement JWT security. This is not something you want to try to write yourself. Here is what Google has to say in its instructions for using Google APIs:
“Note: Given the security implications of getting the implementation correct, we strongly encourage you to use OAuth 2.0 libraries when interacting with Google’s OAuth 2.0 endpoints. It is a best practice to use well-debugged code provided by others, and it will help you protect yourself and your users.” https://developers.google.com/identity/protocols/oauth2/javascript-implicit-flow
Unfortunately, these prewritten libraries are not available in RPG so you will need to add them to your JavaScript, Python, Java or other open source code. (Eradani Connect includes them for you automatically).
2. Authorization
Once you know who the user is, you need to control to what they have access. This can be done simply by limiting the API call to just a specific program, command or SQL Query. Or, if you want to provide more flexibility, you can use Access Control Lists that provide authorization to different sets of functions based on the user.
3. Open Source Modules
As can be seen in the Google post above, Open Source modules are a critical component of a successful, secure API implementation strategy. Open Source modules provide a huge variety of useful functions that you would otherwise have to write yourself. Many API providers like Amazon, Google, UPS, FedEx, etc. provide software development kits (SDKs), that contain all of the complex code necessary for accessing their APIs as modules you can simply use.
However, since using open source means you are using code written by people outside your organization, you do need to pay attention to what you are using. The good news is that there are many tools available to help you choose open source modules wisely.
- Open source package repositories (npmjs, pypi, github, etc.) provide important information on usage of each module. You should check out the popularity of the module (how many people are downloading it), activity (how often is it being updated and how recently), and outstanding issues (are there many outstanding problems). These statistics can help you decide how risky a particular module might be. Popular open source modules are downloaded hundreds of thousands or even millions of times a week by major organizations around the world. You can be confident that they have been thoroughly vetted.
- Source scanning tools can help identify potential vulnerabilities in your software as well as in open source modules. Tools like Appscan and Blackduck will tell you if you have known vulnerabilities in your code (there are many free open source tools for this as well). With the popular open source modules, it is likely that many companies are already running these tools on them.
- With open source, you get the source code. You can always review the code to see what it is doing (although this could be a big job which is why people use source scanning tools).
- Testing tools can help you determine how well an open source module works. The open source you are integrating with your application should be tested along with the code you are writing.
- Package Managers like YUM, RPM and NPM which IBM provides on the IBM i will help you keep your open source modules up to date with the latest security patches. Many of the problems that have occurred with the use of open source have been the result of failures to keep them up to date.
4. Logging and Monitoring
Once you deploy your APIs it is important to monitor usage. This not only will tell you which APIs are valuable to your users and which aren’t, it will also alert you to potential misuse of your APIs.
It is possible for your API to be overwhelmed by call volume either intentionally (as an attack on your system) or by accident (customers make mistakes). In either case, the strategy is similar: Monitor, Identify and Manage. You need to monitor the traffic that is coming into your system and watch for unusual patterns. These might be things like a large sudden spike in traffic from unknown sources (probably an attack) or a large spike in traffic from a particular, known source (probably a user mistake). Using a variety of readily available open source modules, you can monitor for these situations and have them alert you to a potential problem. Once you have identified an issue, you can block the problematic user until they correct the mistake or turn off the API. In the case of an attack, you can adjust the URI for the API and redirect your customers to the new link.
5. Web-based injection attacks, Cross Site Scripting Attacks
There are a variety of ways bad actors can exploit vulnerabilities in your web code to attack your systems. Among other things, they can inject executable strings into input fields and they can take over an authorized connection and use it for their own purposes. Fortunately, there are known coding techniques that can prevent these attacks. You should always review your code for potential vulnerabilities. This guide can help: https://www.lulu.com/content/5678680?page=1&pageSize=4. There are also a variety of commercial and Open Source code scanning tools (Nikto2, QRadar, Netsparker, Appscan, Nmap…) that can identify these issues.
—
A well thought out and structured approach to API security will dramatically reduce your risk from API attacks. By taking care of these areas, your organization can safely take advantage of the promise and business benefits of the API economy. Eradani will soon be publishing a much more detailed whitepaper on API security for the IBM i. To register to receive it, go to www.eradani.com/contact-us/.
At Eradani, we have software solutions and API experts who can help guide you in implementing your API strategy. For more information, visit our website at www.eradani.com or contact us at info@eradani.com.

