Our previous security blogs explored how IBM i systems are often isolated from enterprise security architectures and discussed implementing technologies like Okta for Multi-Factor Authentication. Our last blog focused on the vulnerabilities inherent in using Basic Authentication and the reasons to replace Basic Authentication with more modern authentication methods. Today, I want to focus on a critical aspect of IBM i security that’s becoming increasingly important as organizations expand their integration needs: secure authentication specifically for APIs.
The API Security Imperative
APIs have become essential integration points as IBM i systems become more connected – integrating with web applications, mobile apps, partner systems, and cloud services. However, these same APIs can create significant security vulnerabilities if not properly protected.
I recently spoke with a customer who had just completed building their first set of APIs for their IBM i system. When I asked about their authentication approach, they explained they used basic authentication with IBM i credentials to authenticate API users. This approach, while common, creates serious security risks.
The Problem with Basic Authentication for APIs (Review from our previous blog)
Basic authentication, where API calls include IBM i credentials in every request, presents several critical vulnerabilities:
- Credential Exposure: IBM i credentials are sent with every API call. Even when using HTTPS, these credentials are still transmitted repeatedly, increasing the risk of exposure.
- Credential Proliferation: Any application using these APIs must store IBM i credentials somewhere. These credentials often end up stored in plain text in configuration files, application code, or credential stores outside your control.
- Over-privileged Access: Many organizations grant these API credentials excessive system authorities to make development easier. I’ve seen numerous cases where credentials with *ALLOBJ authority are floating around on various systems – a significant security risk.
- No Granular Control: Basic authentication doesn’t easily allow for limiting what specific API endpoints or operations a client can access.
- No Revocation Mechanism: If credentials are compromised, you must change passwords, potentially breaking many integrations simultaneously.
Modern API Authentication for IBM i
Fortunately, there are better approaches to securing your IBM i APIs. Let’s explore the most effective methods:
Token-Based Authentication
Token-based authentication addresses many of the limitations of basic authentication. Instead of sending credentials with every request, the client authenticates once and receives a temporary token that grants specific access permissions.
Key benefits include:
- Tokens have limited lifespans, minimizing the window of vulnerability
- Tokens can be easily revoked without changing underlying credentials
- Tokens can carry specific permissions and limitations
- Native IBM i user credentials are never stored on client systems
Implementing token-based authentication for IBM i APIs requires a secure token generation and validation system. Eradani Connect simplifies this by providing built-in support for industry-standard token generation, validation, and management.
API Keys with Rate Limiting
For machine-to-machine communications, API keys provide a valuable and safe authentication mechanism. Unlike tokens that expire quickly, API keys are long-lived credentials specifically created for API access.
When implementing API keys, make sure to:
- Generate cryptographically secure random keys
- Implement rate limiting to prevent abuse
- Enable quick revocation and rotation of keys
- Log all API key usage for audit purposes
- Store keys securely using proper encryption
A well-implemented API key system also allows you to monitor for unusual patterns of activity and automatically throttle or block suspicious requests.
OAuth 2.0 Integration
OAuth 2.0 has become the industry standard for the most robust API security. It provides a framework for authorization that separates the authentication process from the API access itself.
With OAuth:
- Users authenticate with an identity provider they already trust
- Your API receives tokens that verify the user’s identity and permissions
- No credentials are ever shared directly with API clients
- Permissions can be highly granular and easily audited
While OAuth implementation is more complex than simpler authentication methods, it provides significant security benefits and aligns with enterprise identity management strategies.
Implementation Considerations
When implementing secure API authentication for IBM i, consider these key factors:
Transport Layer Security: Before focusing on authentication methods, ensure proper transport security is in place. All API communications should use HTTPS with modern TLS protocols (TLS 1.2 or higher) and secure cipher suites.
- Token Storage and Management: If implementing token-based authentication, carefully consider how tokens are stored and managed. Tokens should:
- Be stored in memory rather than persistent storage
- Include appropriate expiration times
- Contain only necessary information
- Be validated on every request
- Authorization Implementation: Authentication (verifying identity) is only half the equation – you also need authorization (controlling what authenticated users can do). Implement proper authorization checks within your API layer to enforce access controls based on the following:
- User identity and roles
- API endpoint accessed
- Operation performed
- Time of day or other contextual factors
- Monitoring and Logging: Implement comprehensive logging of all API authentication activities. This should include:
- Authentication attempts (successful and failed)
- Token issuance and validation
- API key usage
- Authorization decisions
These logs should integrate with your enterprise security monitoring systems for visibility and alerting.
Real-World Implementation Example
One of our manufacturing customers recently transitioned from basic to token-based authentication for their IBM i APIs. They integrated their IBM i inventory system with their e-commerce platform and initially implemented basic authentication with IBM i credentials.
After reviewing their security architecture, we identified the risks in their approach and helped them implement a token-based solution with Eradani Connect. The implementation:
- Created a secure token service for generating and validating JWTs (JSON Web Tokens)
- Modified their API gateway to validate tokens instead of checking credentials directly
- Implemented proper token lifecycle management with appropriate expiration times
- Added comprehensive logging of all authentication and authorization decisions
- Connected this logging to their enterprise SIEM (Security Information and Event Management) system
The result was a significantly more secure integration architecture with better visibility and control, all without any changes to their core IBM i applications.
Best Practices for Secure API Authentication
As you evaluate your IBM i API authentication approach, keep these best practices in mind:
- Never transmit IBM i credentials over the network: use tokens or other secure authentication methods instead.
- Implement the principle of least privilege: ensure API credentials have only the minimum necessary authorities.
- Use short-lived tokens: the shorter the token lifespan, the smaller the window of vulnerability.
- Implement proper token validation: check every request’s signatures, expiration times, and permissions.
- Ensure secure key storage: any secret keys used for token signing must be properly secured.
- Maintain a complete audit trail: log all authentication and authorization decisions for security monitoring.
- Plan for credential rotation: implement processes for regularly rotating all API credentials and keys.
- Implement rate limiting: protect against brute force attacks by limiting authentication attempts.
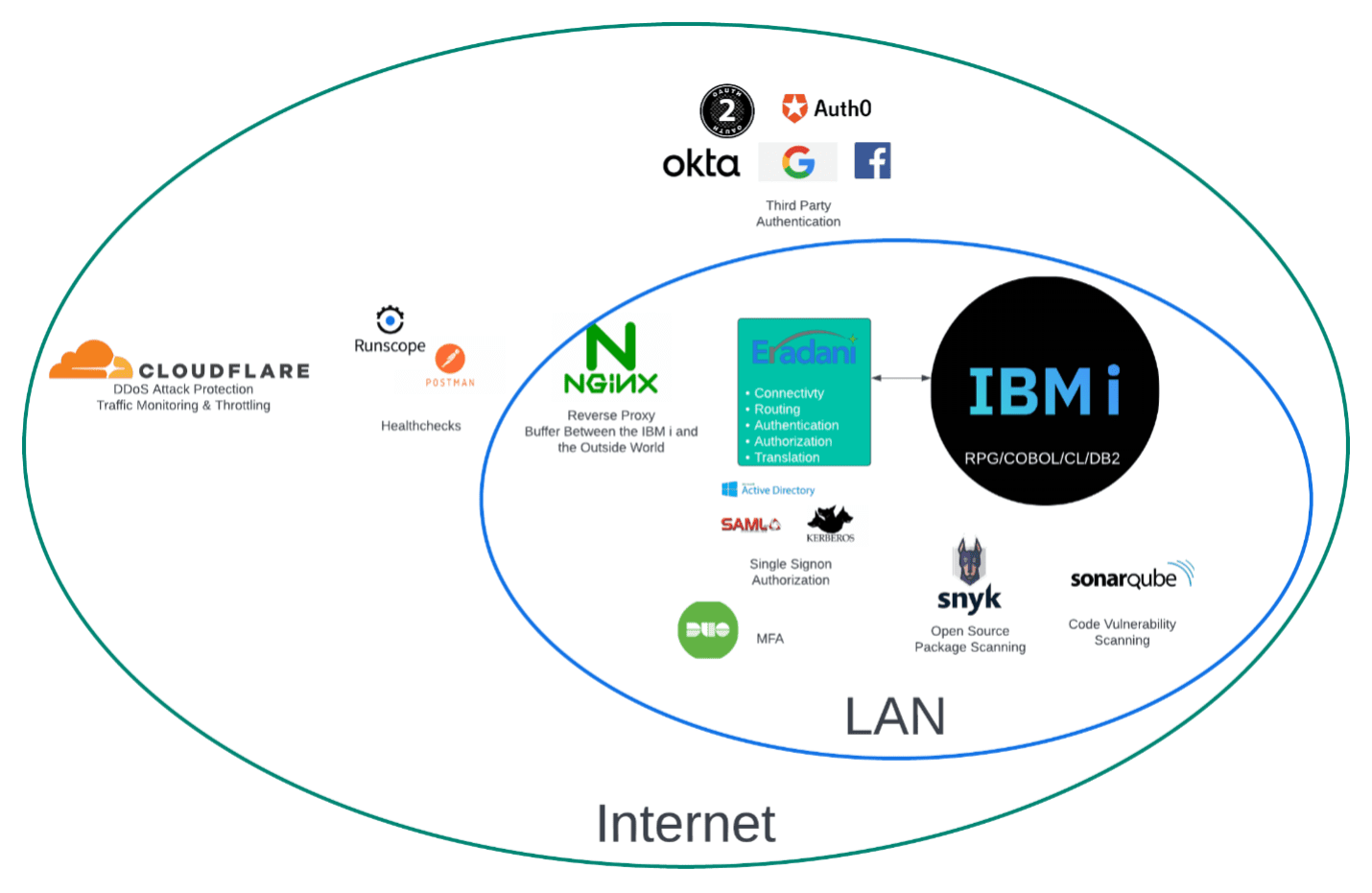
With Eradani Connect, you can easily plug your IBM i into the entire API security ecosystem:
Moving Forward
As you expand your IBM i integration capabilities through APIs, securing those APIs should be a top priority. Consider the following questions:
- Are you still using basic authentication with IBM i credentials for your APIs?
- Do you have a process for managing API credentials and ensuring they have appropriate authorities?
- Can you quickly revoke access for specific API clients if needed?
- Are you monitoring and logging all API authentication activities?
The answers to these questions will help guide your journey toward more secure API authentication for your IBM i systems.
At Eradani, we specialize in helping IBM i organizations implement secure integration architectures that protect their critical systems while enabling the connectivity modern businesses require. Our Eradani Connect platform provides built-in support for modern authentication methods, making it easy to implement secure APIs without compromising your IBM i security.
In our upcoming webinar, “Beyond Passwords: Modern Authentication & Authorization for IBM i,” we’ll dive deeper into implementation details and demonstrate how to set up these security mechanisms. I hope you’ll join us in continuing this important discussion on securing your IBM i environment.

Dan has spent over thirty years leading companies that help customers implement new technologies in legacy environments. Previously, Dan led worldwide software development groups that built highly successful modernization and DevOps tools and was the CEO of Aldon, the leading provider of DevOps tools to the IBM i marketplace. To learn more about Eradani’s offerings, reach out to us today!

