Security
Secure Enterprise Integration for Mission-Critical Systems
Enterprise Security Integration
Remove security islands in your enterprise with native integration to enterprise MFA providers (like Okta and Duo), enterprise SSO solutions (like Microsoft Entra, formerly Active Directory, and SailPoint), secure API authentication, and unified security monitoring. Implement modern security without disruption through token-based authentication, OAuth2 verification, and centralized monitoring and alerting that transforms security outliers into fully compliant systems.

Performance-Optimized Security
Deploy advanced security measures with millisecond response times, ensuring robust protection without performance degradation while leveraging open standards that prevent vendor lock-in.

Comprehensive Visibility
Gain complete visibility into your security landscape through integration with enterprise-standard monitoring tools (such as Data Dog, Grafana), detailed audit trails, and real-time security alerting.
DevOps Security
Protect your systems from code vulnerabilities with automated security scanning, enforced approval processes, and secure deployment workflows. Know who’s making changes to your code, implement proper authorization controls, and validate code for security issues before it reaches production. Secure your development pipeline with the same enterprise standards used across your organization.
SECURITY SUCCESS CASE
Manufacturing Company Integrates IBM i with Enterprise MFA
CHALLENGE
A leading manufacturing company faced a significant security dilemma. Their IBM i systems contained mission-critical data and ran core business applications, but existed as a security island separate from their enterprise-wide authentication strategy. Their security team had successfully implemented multi-factor authentication (MFA) across all other platforms, but the IBM i remained an outlier, requiring separate credentials and lacking integration with their enterprise identity provider. This created security risks, compliance issues, and administrative overhead as users needed to authenticate separately for IBM i access.
SOLUTION
The company implemented Eradani Connect to bridge the gap between their IBM i environment and their enterprise identity management system. The solution:
Integrated their IBM i authentication with their existing enterprise MFA provider
Eliminated the transmission and storage of IBM i credentials
Implemented token-based authentication for all API connections
Connected IBM i security events to their enterprise monitoring dashboard
Enabled single sign-on capabilities aligned with their zero-trust security model
Eradani's Integration Security Maturity Model
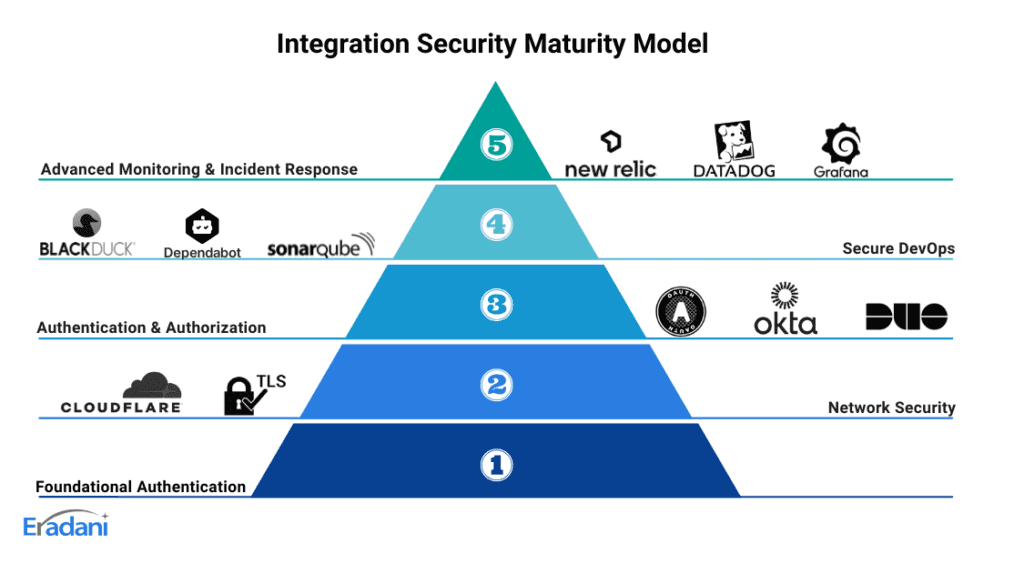
Eradani has developed a comprehensive Integration Security Maturity Model that helps organizations assess their current security posture and chart a path toward a more robust and integrated security approach. To learn more, check out The IBM i Security Maturity Model: Protecting Your Mission Critical Systems.
Do You Have an IBM i? We're Here to Help.
Eradani Connect transforms IBM i systems from security vulnerabilities to secure enterprise assets by implementing advanced security controls. The solution provides:
- Native integration with enterprise MFA providers (like Okta and Duo)
- Support for modern authentication methods (OAuth2, tokens)
- Integration with enterprise SSO providers (like Microsoft Entra/Active Directory, SailPoint)
- Elimination of the dangerous practice of transmitting IBM i credentials
By creating a secure API layer around your IBM i, Eradani enables role-based access control, granular authorization, and integration with enterprise security monitoring dashboards.
This approach allows organizations to standardize their security approach across all platforms, removing the “IBM i security island” while maintaining robust security and high performance. With Eradani Connect, your IBM i becomes a full participant in your enterprise security architecture.
IBM i Integration Security: A Practical Journey to Modern Security
Our comprehensive four-part webinar series guides IBM i users through a practical journey from understanding security vulnerabilities to implementing modern authentication, secure DevOps practices, and advanced monitoring, helping organizations integrate their IBM i systems into enterprise-wide security architecture rather than treating them as isolated security islands.
How Our Customer Benefits From Eradani Connect Security

Enhanced security posture through enterprise-wide MFA implementation and elimination of security silos across systems.
Simplified compliance reporting and auditing with consistent authentication methods across all platforms.
Reduced security management overhead by integrating all systems into the existing enterprise security architecture instead of maintaining separate solutions.
Want to Know More About
the Comprehensive Approach to Securing Your Systems?
Schedule a demo to see how Eradani Connect can help!
We are happy to answer any questions you may have.

