In our previous security blogs, we’ve discussed how IBM i systems are often treated as “security islands” within enterprise architectures. Today, I want to tackle a practical solution to this problem: integrating your IBM i with Okta for Multi-Factor Authentication (MFA) and Single Sign-On (SSO).
Why IBM i Security Integration Matters
Almost weekly, I meet with CIOs who confidently tell me their enterprise is fully protected by modern security standards – until I ask about their IBM i systems. Then comes the pause, followed by, “Well, those are… different.”
This security isolation creates serious vulnerabilities. Most of today’s attacks originate from inside company networks, often from an internal device that has been compromised. By treating IBM i as a security outlier, organizations create gaps in their security posture right where mission-critical data lives.
The Enterprise-Wide Approach to Security
Modern enterprise security demands a unified approach where IBM i systems participate fully in your security architecture. This means:
- Leveraging the same MFA-based security provided to other platforms
- Integrating with existing enterprise MFA providers like Okta, Duo, Entra, etc.
- Eliminating duplicate authentication processes
- Providing consistent security experiences across all platforms
Understanding Authentication Components
Before we dive into the Okta integration, let’s clarify some terminology:
- Authentication determines who a user is and if they’re who they claim to be
- Authorization determines what an authenticated user is allowed to do
- Multi-Factor Authentication (MFA) requires users to verify identity through multiple factors: something they know (password), something they have (device), or something they are (biometrics)
- Single Sign-On (SSO) allows users to access multiple applications with one set of credentials
The Okta Integration Advantage
Okta has emerged as a leading Identity and Access Management (IAM) solution, and for good reason. By connecting your IBM i with Okta, you gain:
- Enterprise-wide security consistency – your IBM i follows the same security protocols as other systems
- Enhanced protection against credential theft – even if passwords or devices on the network are compromised, MFA prevents unauthorized access
- Simplified compliance reporting – centralized authentication logs across all systems
- Reduced administrative overhead – no need for separate IBM i security management
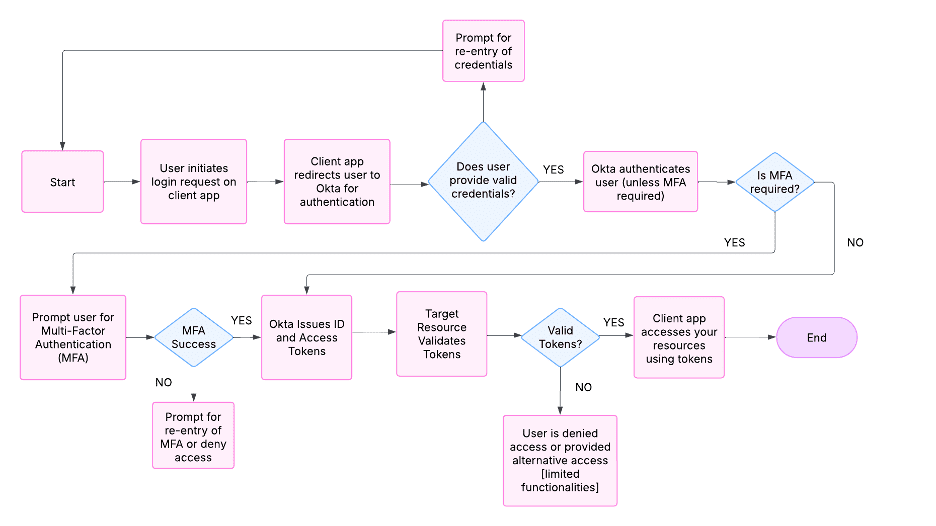
How the Integration Works
When connecting IBM i to Okta through Eradani Connect, here’s what happens behind the scenes:
- A user attempts to sign on to their 5250 session
- Their initial program makes an outbound call through Eradani Connect to Okta’s authentication services
- Okta verifies the user’s identity through their configured MFA method (push notification, OTP, etc.)
- An authentication token is returned to the IBM i application
- Based on this result, the user is either granted access or denied
The beauty of this approach is that it leverages Okta’s well-maintained SDKs and APIs while requiring minimal changes to your IBM i applications.
OKTA Authentication Flow:
Implementation Considerations
When implementing Okta integration for your IBM i, consider these best practices:
- Establish Fallback Procedures: Create maintenance user profiles that bypass MFA requirements. This provides a critical backdoor in case Okta services become unavailable, preventing accidental lockouts.
- Add Service Monitoring: Implement health checks for Okta services. Your authentication process should include logic to verify that Okta is available before attempting authentication calls.
- Plan for Automation: Some IBM i processes are automated and don’t involve human users. These should be identified and handled differently, as MFA is designed primarily for human authentication.
- Device Strategy: For warehouse environments or areas where personal devices are prohibited, consider hardware token options that generate time-based one-time passwords (TOTP). These physical tokens can cost around $20 per user but provide a reliable second factor without requiring smartphones.
Real-World Success
One of our manufacturing clients recently integrated their IBM i environment with Okta, bringing 5250 terminal sessions under the same security umbrella as their web applications. By implementing MFA through Eradani Connect, they achieved several key benefits:
- Security team visibility into IBM i authentication events
- Elimination of plain-text IBM i credentials on other systems
- Consistent security experience for users across all platforms
- Simplified compliance reporting for security audits
Their CIO noted: “For the first time, our IBM i is no longer treated as a security exception. It’s fully integrated into our zero-trust architecture.”
Beyond MFA: The Complete Security Picture
While MFA is a critical component, remember that it’s just one part of a comprehensive security strategy. A complete approach should also include:
- API layer security to protect calls between systems
- Network configuration security to manage how devices connect to your IBM i
- Credential management to eliminate storing IBM i profiles and passwords on external systems
- Authorization frameworks to control what authenticated users can access
Getting Started
If you’re ready to integrate your IBM i with Okta for MFA and SSO, here are the steps to begin:
- Assess your current authentication landscape – What systems and applications need to be integrated?
- Identify user types and access patterns – Who needs access to what, and through which channels?
- Determine MFA requirements – Will you use push notifications, authenticator apps, or hardware tokens?
- Plan your integration architecture – How will authentication flow between systems?
At Eradani, we’ve helped numerous organizations successfully integrate their IBM i systems with enterprise security solutions like Okta. The result is a more unified, secure environment that treats IBM i as a full participant in your security architecture, not as an outlier.
Remember, in today’s security landscape, having strong authentication on most of your systems isn’t enough. True security requires consistent, enterprise-wide protection that includes every platform – including your IBM i.
For more information on integrating your IBM i systems with enterprise security solutions, contact us at Eradani. We’ll help you protect your mission-critical systems while maintaining the robust performance you expect from IBM i.

Dan has spent over thirty years leading companies that help customers implement new technologies in legacy environments. Previously, Dan led worldwide software development groups that built highly successful modernization and DevOps tools and was the CEO of Aldon, the leading provider of DevOps tools to the IBM i marketplace. To learn more about Eradani’s offerings, reach out to us today!

