It’s scary how many IBM i users I’ve spoken to in the last few months whose networks have been hacked. Unfortunately, the frequency of those calls is growing rapidly. It is no longer safe to assume that if you don’t connect your IBM i to the internet, you will be safe. If any of the personal computers people use to connect to the IBM i also have access to the internet and email, you could be exposed. The good news is that there are well-proven steps you can take to protect your systems.
Many network attacks today are perpetrated through a compromised machine on the network. Someone clicks on a bad link in an email or visits a malicious website and their PC gets infected with malware. That malware can then start searching the machine for credentials it can use to access the IBM i. Even if you have disabled guest access to the IBM i, the hacker can retrieve real, valid credentials. So, where would the hacker find valid credentials? The problem for IBM i users is that many are using Basic Authentication for connecting browser applications and APIs to the IBM i. Out of the box, Basic Authentication creates two major vulnerabilities.
- Basic Authentication sends user credentials (in this case, IBM i User IDs and Passwords) as 64-bit encoded headers. Anyone who intercepts a message can easily decode the 64-bit encoding and retrieve the credentials. 64-bit encoding is not encryption – the algorithm to decode it is published and well-known.
- To avoid forcing the user to sign in repeatedly, Basic Authentication stores the user credentials in the browser – another place where they can be discovered.
You can address the first issue by ensuring that all communications with your IBM i are made using TLS (https). By using TLS, the credentials will be encrypted during transmission and unreadable by anyone who might intercept the message. You can also generate and use API keys and secrets rather than native IBM i credentials to identify the user so no IBM i credentials are being transmitted.
The second issue is more difficult. Unfortunately, even if you are using API keys instead of IBM i credentials, those can still be discovered and used. If those keys are still being mapped to an IBM i user ID, the hacker could still get access to the IBM i.
To help reduce that exposure, you can use JSON Web Tokens (JWTs) for authentication. JWTs are generated during the initial sign-on and are used for all access after that. The original credentials then are never stored on the machine and thus cannot be discovered. The JWTs can be set to expire automatically so even if a hacker could get one, they would only be useful if they were used during the time they were active. The hacker would need to be targeting you specifically and watching what you were doing.
You can even close that last loophole by adding multifactor authentication (MFA). We have IBM i customers who have done this even for their 5250 sessions. The user signs on with their user ID and password but before allowing the connection, the system sends a message to their phone that they must respond to. Only after getting the response, does the connection get completed.
When using APIs to access the IBM i for machine-to-machine communication, there may be no user involved to provide MFA. In that case, it is best to eliminate Basic Authentication altogether and implement third party authentication like OAuth2. With OAuth, a third party (like Google, Facebook, OKTA, etc.) verifies that the user is who they say they are. The third party then provides tokens that are used for the communication.
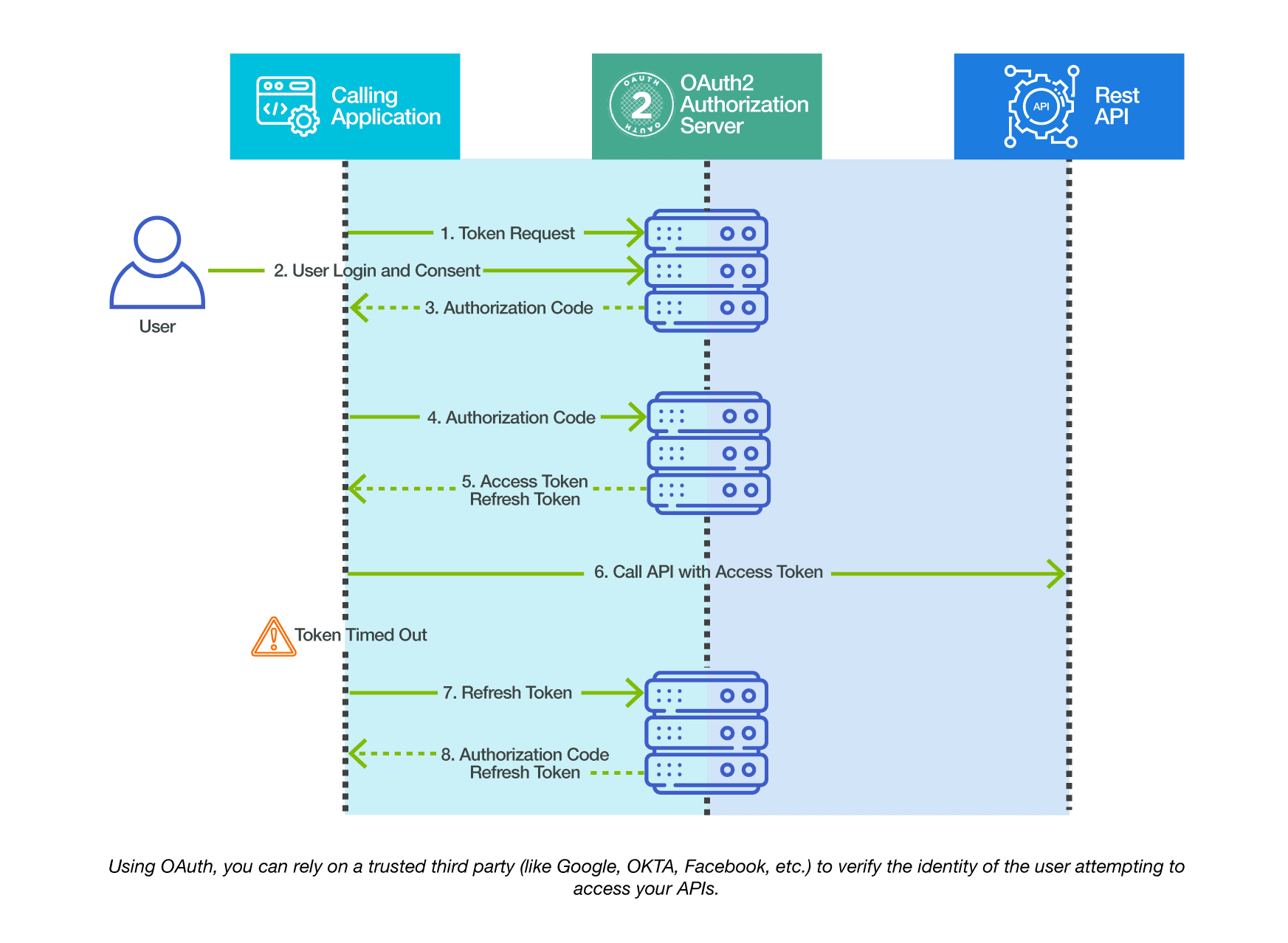
Adopting these new technologies for the IBM i does not have to be difficult. Most of the code necessary has already been built for you in open source modules that are supported on the IBM i. You can simply download these modules and integrate them into your APIs. By using these techniques, you can open up your IBM i to new technology while keeping it secure.
To learn more about securely API enabling your IBM i, check out our recorded webinar at: https://eradani.com/securely-api-enable-your-ibm-i-applications/
There is also a great article on IBM i security by Robert Andrews here: https://community.ibm.com/community/user/power/blogs/robert-andrews/2021/06/08/ransomware-and-ibm-i

